In the past, I’ve tried to decompile the game’s code using RetDec.
While I was successful in translating the games binary into some pseudo-code, I couldn’t really do anything with it.
Recently, the NSA declassified and released a powerful reverse-engineering tool called Ghidra.
In addition to that, someone created a language definition for Ghidra, containing specific instructions for the GameCube’s Gekko processor.
How to Import AWL code into Ghidra
Extracting the Executable From the Game
To analyze AWL (or AnWL) code with Ghidra, you’ll need to extract the game’s main executable.
This can be named Start.dol, boot.dol, or main.dol, depending on your tool of choice.
The executable can be extracted using Dolphin by right-clicking on your ISO and selecting “Properties”
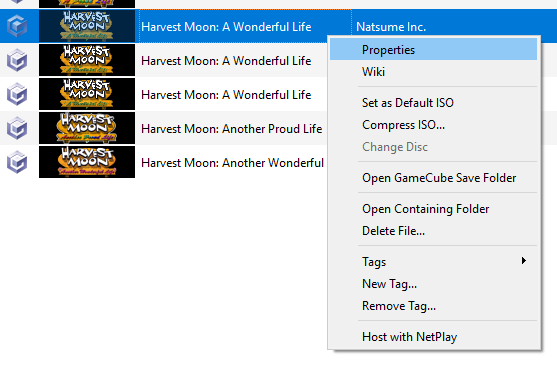
Then, in the Filesystem tab, right-click the Disc and select “Extract System Data”
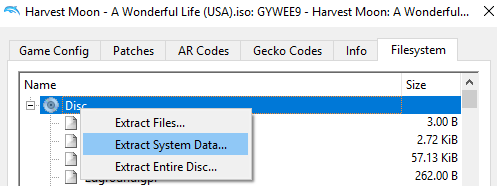
You’ll find the extracted executable named main.dol in your chosen folder.
Converting the Executable to a Better Format
Gamecube executables are typically in a DOL format. While this can, in theory be analyzed, it’s much easier for Ghidra (and other tools) to analyze an ELF-format file.
To do this, we can use a tool aptly called DolTool.
Simply copy your main.dol file into the DolTool directory and open up a command prompt in the folder. Then run the following.
DolTool.exe -e main.dol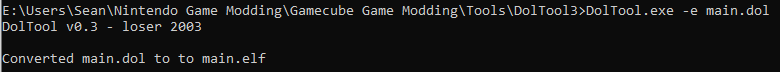
Importing your ELF into Ghidra
Create a new Ghidra project, then select File -> Import, and select your new main.elf file.
In the following screen, select the “Executable and Linking Format” format and “PowerPC:BE:32:Gekko_Broadway:default” language

Analyzing main.elf
Finally, right-click your newly imported main.elf file and select “Open in Default Tool”
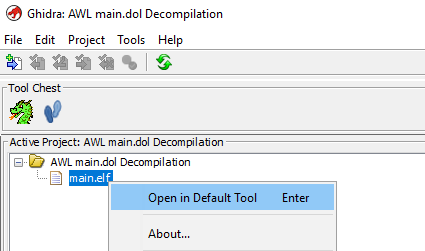
The file should then open up in CodeBrowser and prompt you to analyze it.
From here, you’re free to use the program to analyze the code and it’s functions.

I don’t have much experience with reverse engineering, so you’re on your own from this point forward.
This is awesome news. Found this blog by searching “gamecube decompiler”. I am interested in modding Super Mario Sunshine and possibly even recompiling it for x86-64. I’m assuming this is somewhat based on Ida? Looks better and more advanced, should be easier to analyse gc games noe.
LikeLike
It’s a separate tool from IDA developed by the American NSA, but undoubtedly takes some inspiration from IDA. It was released to the public as open source earlier this year.
It’s geared towards software research (i.e. figuring out how code is supposed to work). A lot of people in the GC/Wii hacking community have been looking into using it and have made Ghidra function libraries for various Gekko/Broadway assembly code.
It would likely take months or years to do something like recompile for a game for a different architecture, so your best bet for Sunshine would be to emulate in Dolphin. Theres also a significant Sunshine modding community with tutorials on modifying various files from the game.
LikeLike